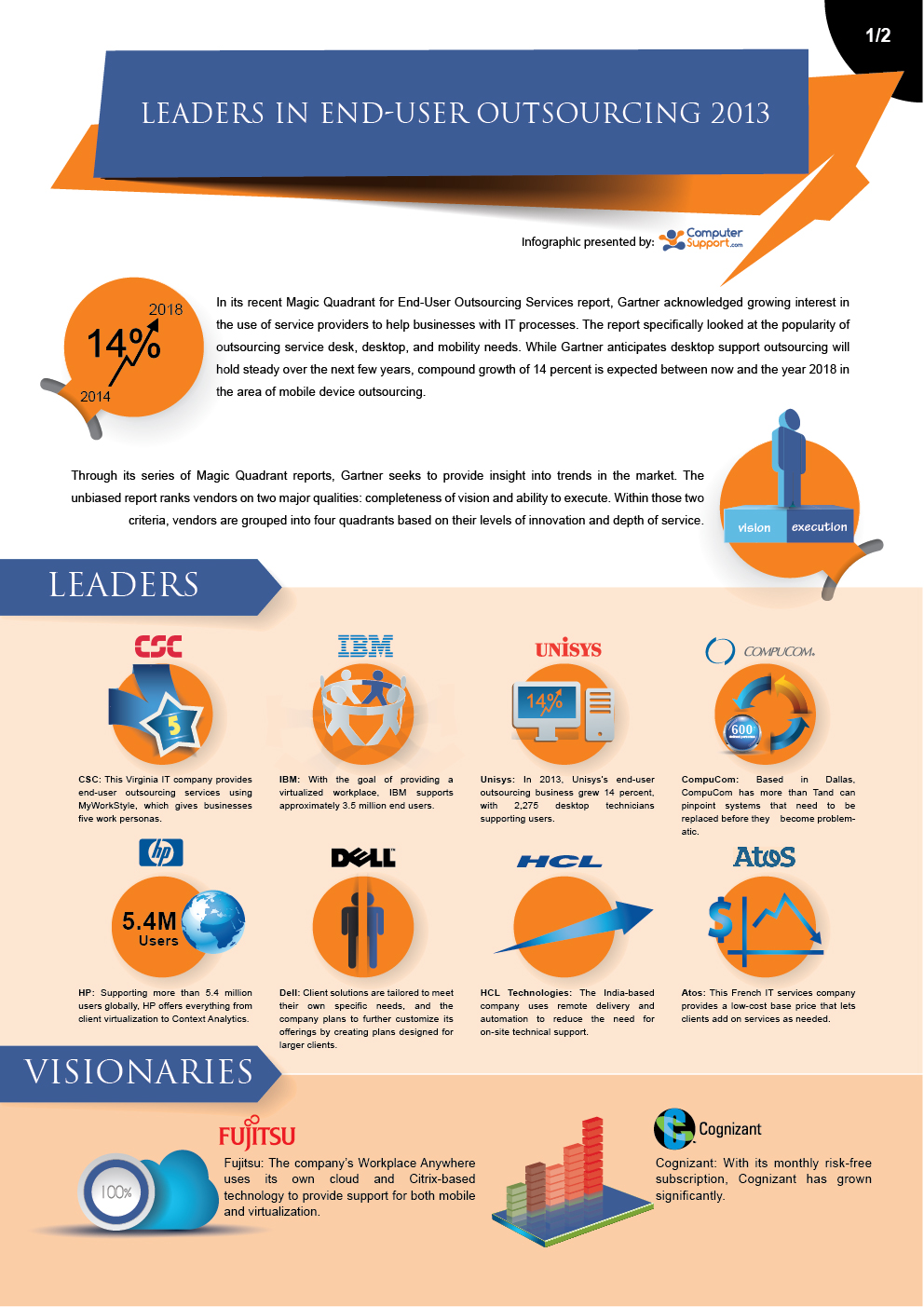
Top 10 Cloud Myths and How They will Impact Your Business
Are you confused how the ‘Cloud’ can benefit your organization? If so, you’re among millions of senior executives who want to known the benefits of moving their IT networking to the Cloud.
A recent Gartner report reveals some of the worst misinformation surrounding Cloud computing, and this high-resolution Top 10 Cloud Myths Infographics will give you a great overview of it!
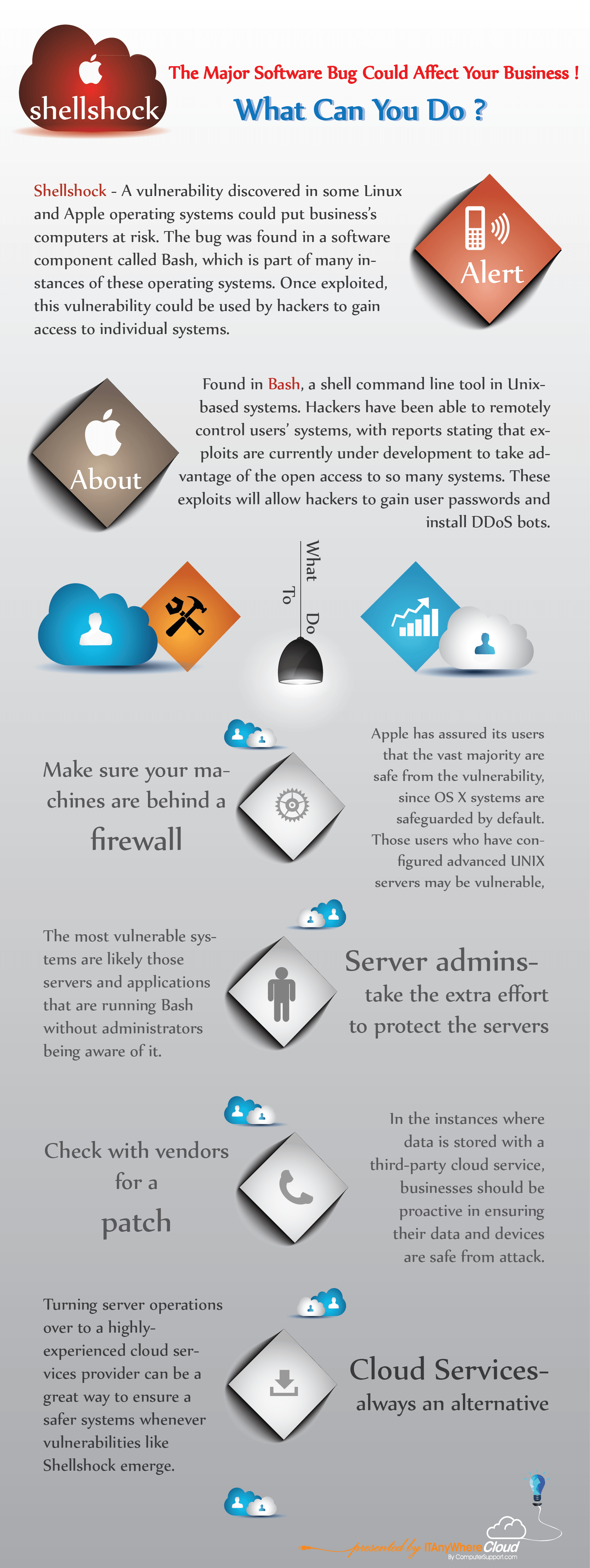
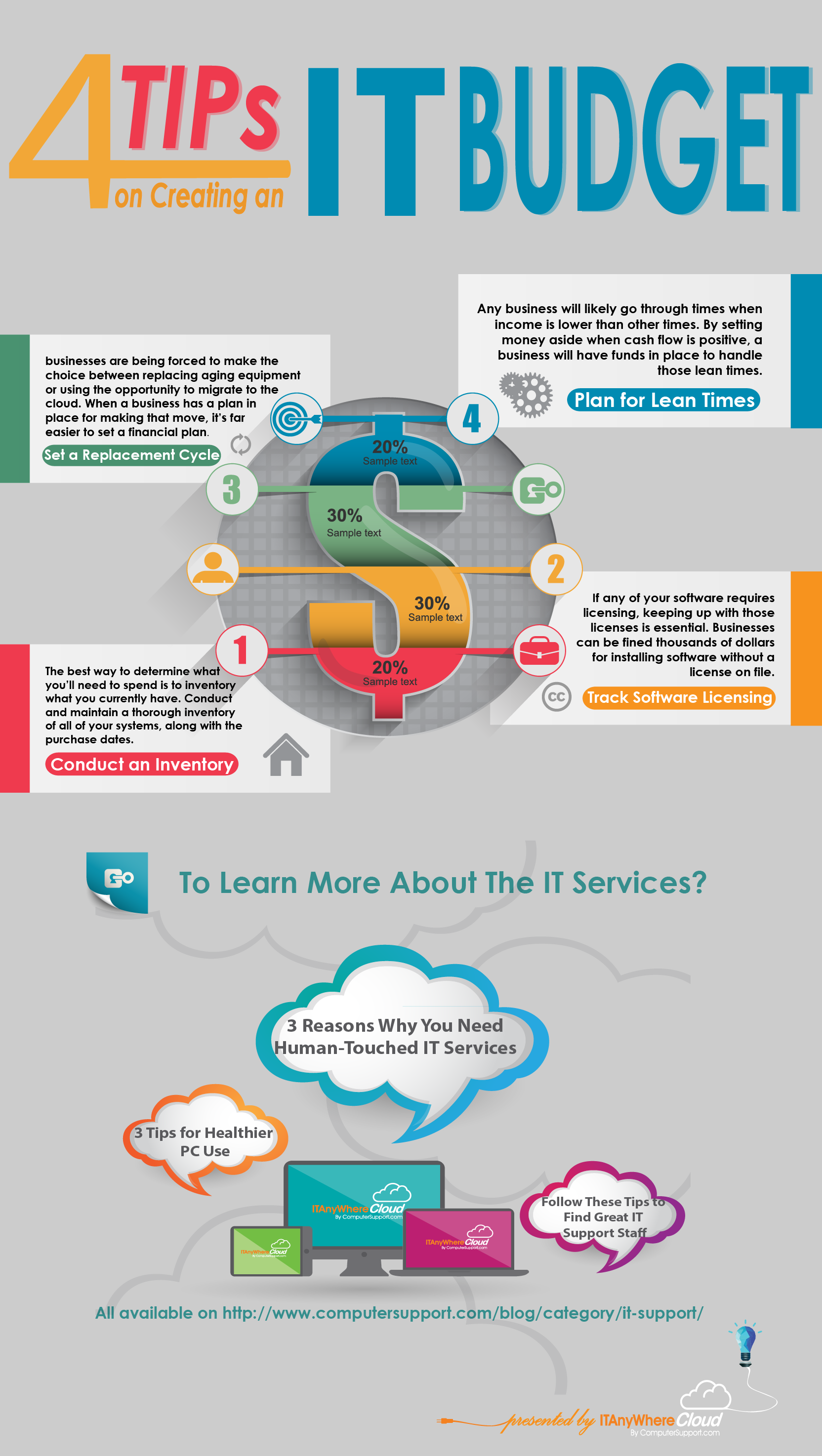
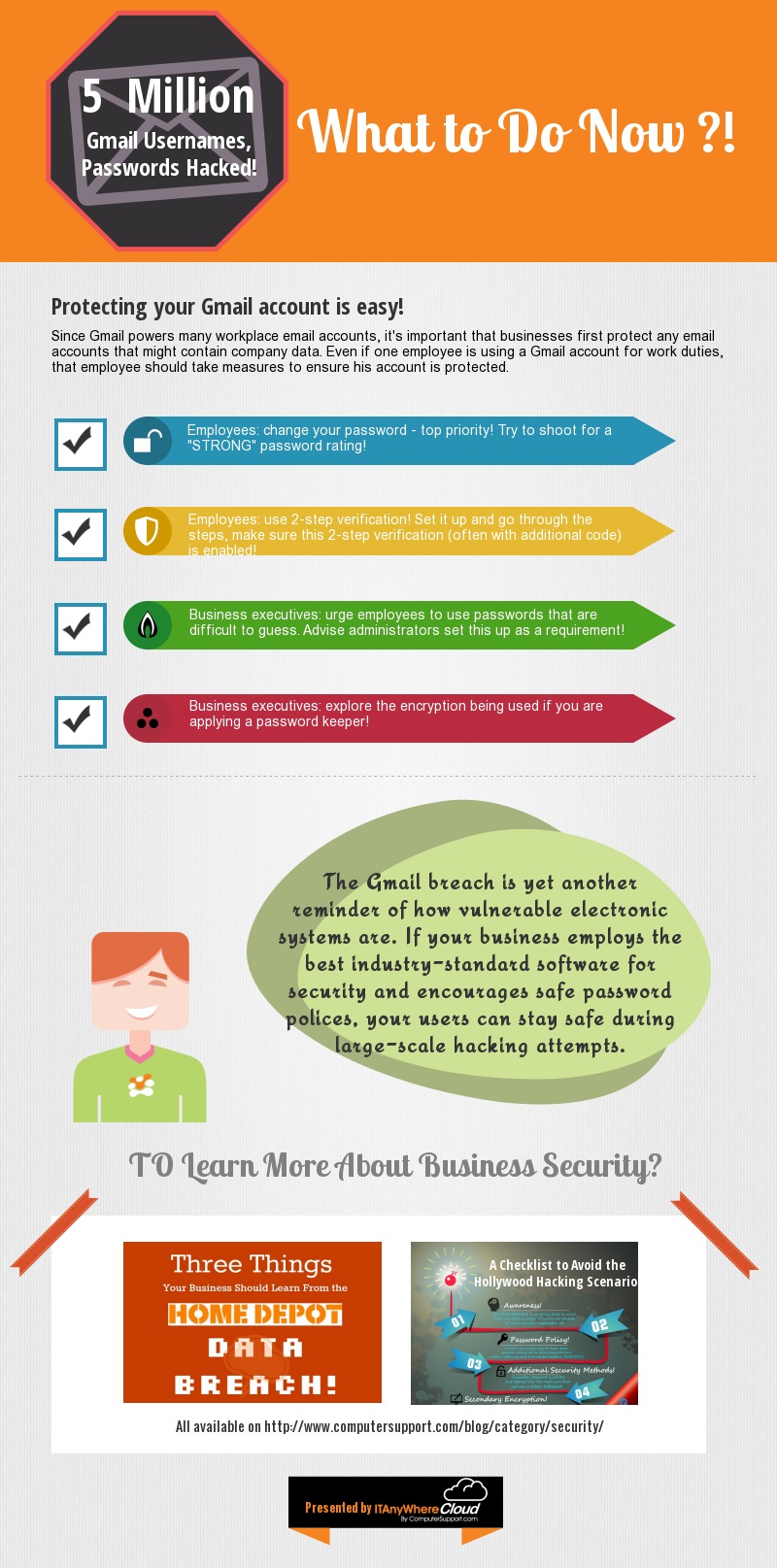
#10 – The Cloud Will Reduce Your Expenses
This is not always true. In fact, in some cases, migrating your network over to the Cloud may involve costly integration. It’s wise to speak with authority cloud service providers Long-term, you can reduce your costs. However, it’s important you understand the initial set-up of your IT infrastructure will require a capital investment.
#9 – If You’re Not Using The Cloud You’re Missing Out
Although the Cloud can enhance how your employees access company files and networks, there’s been enormous advertising efforts by CSPs to make you a convert. We recommend doing a network audit of your system before determining whether or not your company will benefit by migrating over to the Cloud.
#8 – Is The Gartner Report Pro Cloud?
Yes and no. If you read the Gartner report, you’ll notice it does provide reasons why the Cloud is wise for SMBs. However, the report does advocate some of the challenges companies will need to consider such as mapping out your current business IT needs. Then evaluate if upgrading your resources to the Cloud will enhance employee access to your network.
#7 – Your Cloud Network Isn’t Secure
No network (wired or wireless) is secure unless your IT technicians have properly installed security encryption measures and protocols.
#6 – Security Is Limited With Cloud Networking
Although this has become a controversial issue, many CSPs report very few security breeches with Cloud networks. Despite 2014’s detrimental security breeches by large companies such as Target, Sony and Home Depot, most network infiltrations are still bypassed through poorly-designed firewalls and gateways.
#5 – Cloud Integration Can Replace Data Centers
This is a widely-accepted misconception about the Cloud. Yes, you can enhance your network but the Cloud will not replace your data center.
#4 – Cloud Migration Will Resolve Expired Windows 2003 Support
This is an issue many companies are facing. According to Insight Enterprises, 24 million servers are still running the expired version of Windows 2003. In July of 2014, Microsoft discontinued support for Win 2003. Therefore, companies hoping an upgrade to the Cloud will resolve their expired Win 2003 OS version may be surprised to find out it’s not the case.
#3 – Outsourcing Your Cloud Migration Is Risky
Not true. Although, it is vital you work with a trusted provider. Our infographic outlines what you need to know about Cloud management.
#2 – The Gartner Report Is Misleading
Although the Gartner report outlines many of the benefits using the Cloud, it’s important to note any IT upgrade your company considers should be approached with advanced research.
#1 – Get On The Cloud Or Be Left Behind
Some companies may not be ideal candidates to integrate their networks to the Cloud. We recommend analyzing your legacy servers and run a cost-benefit analysis report to determine if reduced expenses moving your network to the Cloud are viable.



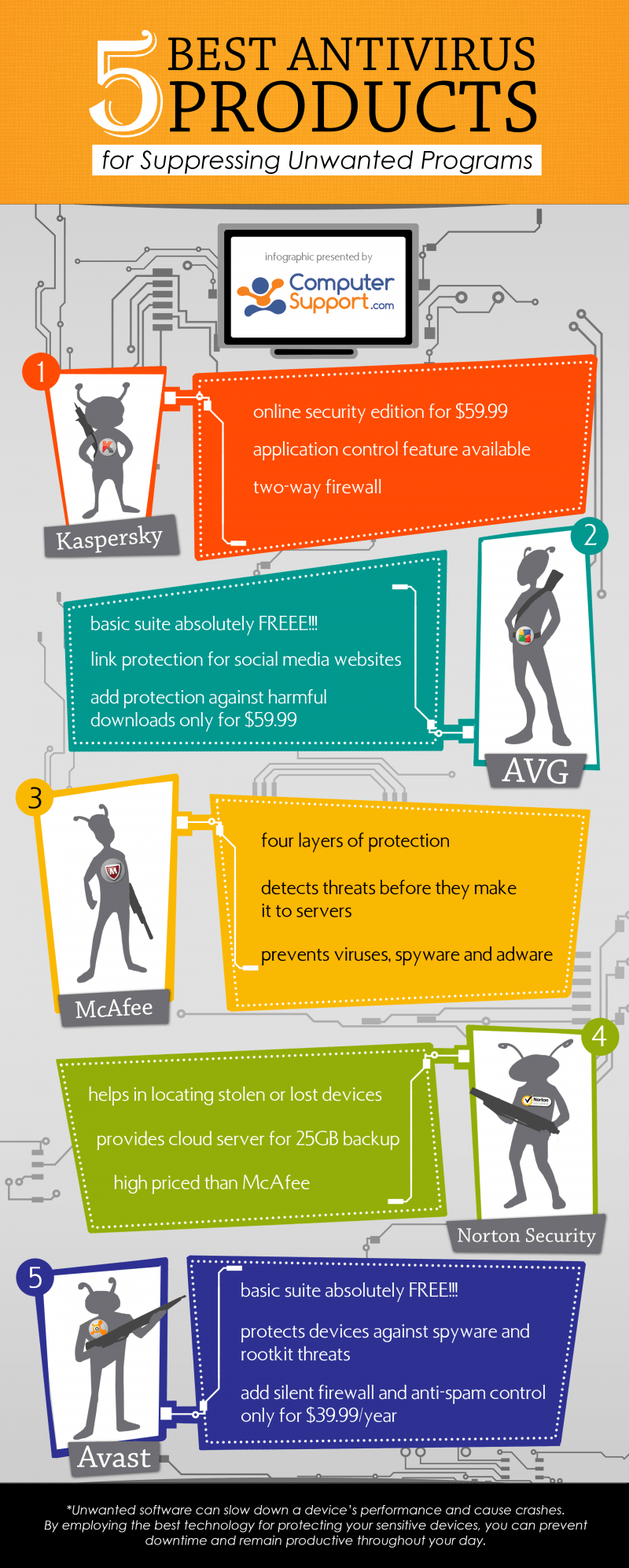 As a busy professional, you rely heavily on your electronic devices throughout the day. Whether you’re trying to find the best place to take a client for lunch or conducting research for a report, it’s important that your internet browsing experience be as painless as possible. Unfortunately, the web too often has other plans for you, as websites push unwanted programs and applications to your device.
As a busy professional, you rely heavily on your electronic devices throughout the day. Whether you’re trying to find the best place to take a client for lunch or conducting research for a report, it’s important that your internet browsing experience be as painless as possible. Unfortunately, the web too often has other plans for you, as websites push unwanted programs and applications to your device.