Beware of Phishing
In recent weeks, we have seen a huge increase in hostile activities, especially phishing, spear phishing, whaling, email phishing, clone phishing, so we decided to take a step forward and show our readers how to spot such attempts, the latest hacking methods, tools, etc.
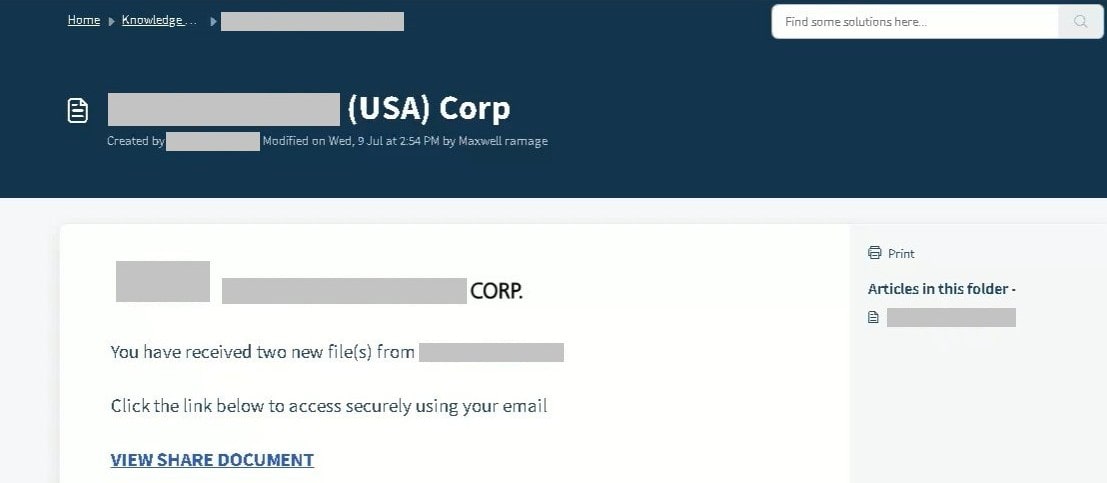
File Sharing Applications
Cybercriminals will often share a malicious link to a document using a customized email which usually includes the name of the target company.
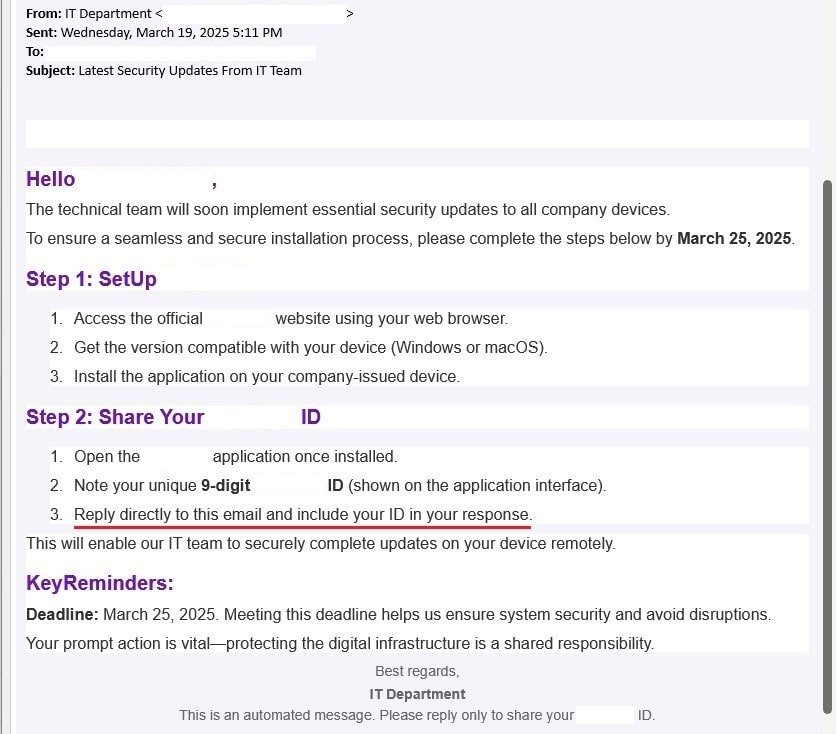
Fake IT Requests
There are many methods that attackers may use to trick people into clicking a link or downloading a malicious file. The example below is just another iteration you should look out for.
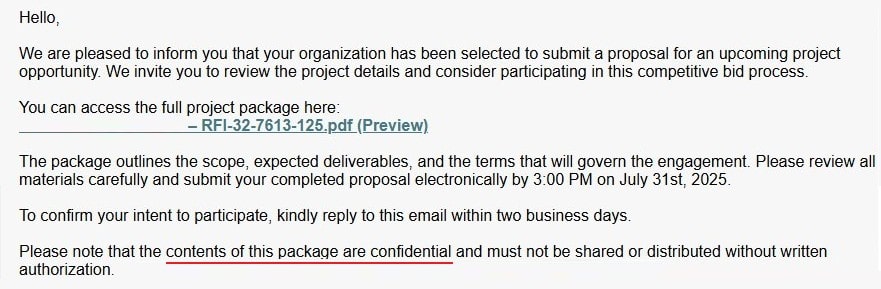
Time Deadline And “Confidential”
Creating a sense of urgency is one of the clues of a hacking attempt. Another one is confidentiality because keeping the target isolated is crucial for the success of the attack.
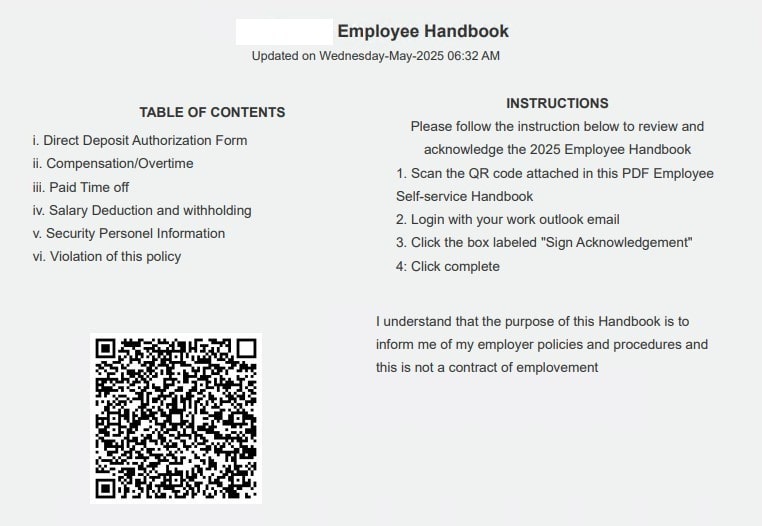
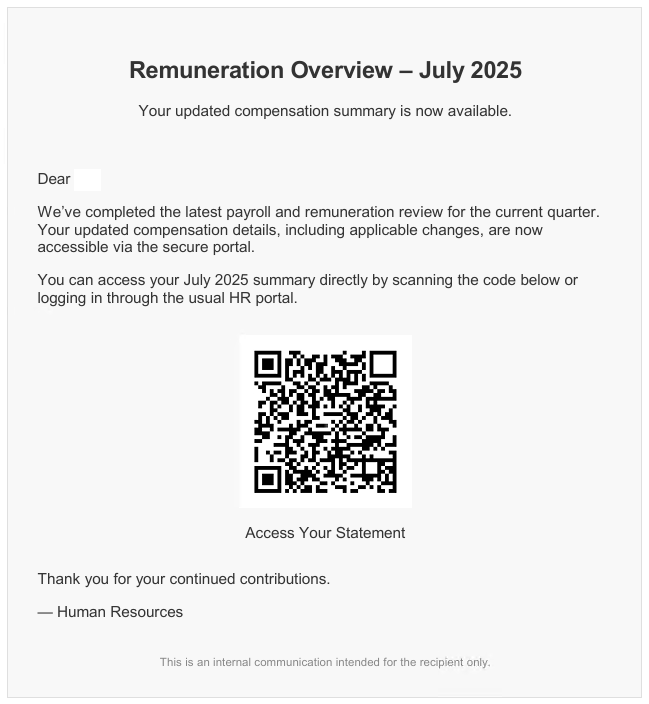
Watch Out For QR Codes!
QR codes have picked up steam. The following three screenshots describe hacking attempts where cybercriminals tried to create the perfect context to convince the recipients to scan these fraudulent QR codes leading the victims to malicious websites.
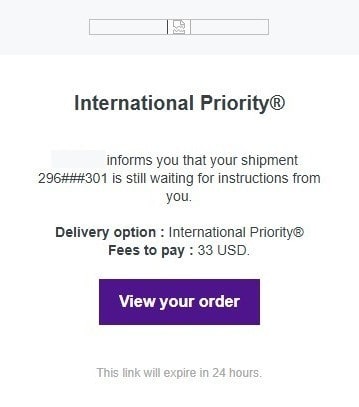
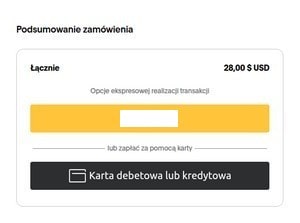
Shipping Phishing Scams
We are seeing increasingly more shipping phishing scams.
Clicking “View Your Order” will take the victim to this page:
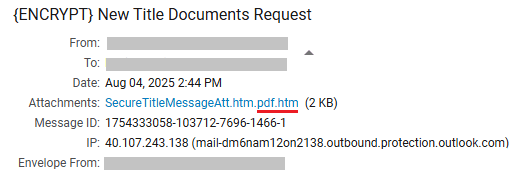
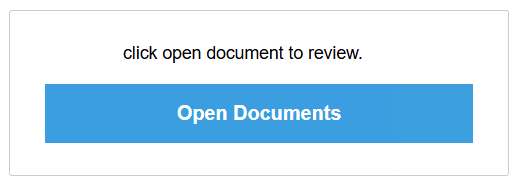
Fraudulent Attachments
Beware of suspicious attachments, e.g.
Clicking the attachment would get the user to this .htm file pointing the victim to the phishing website.
Trial Accounts
Cybercriminals can sign up for trial accounts just to share a phishing document.
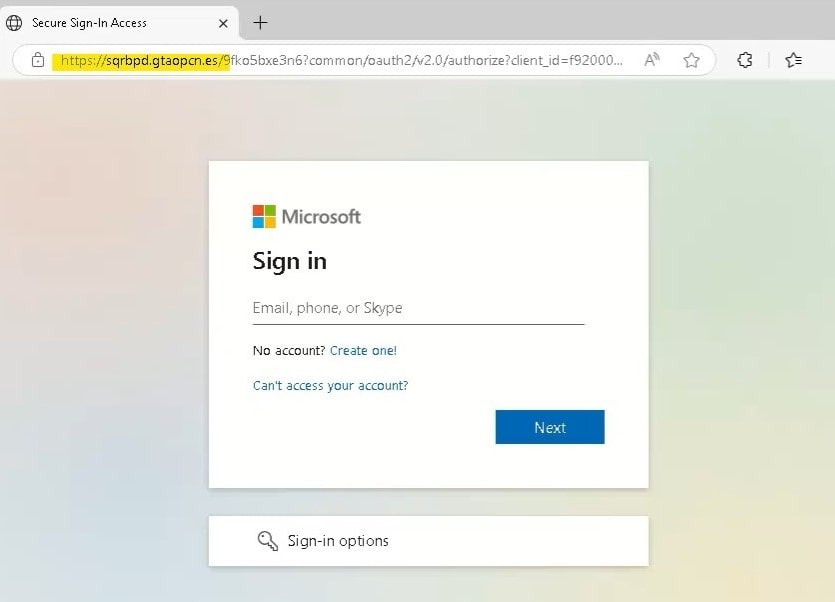
Fake Sign-In Pages
The strategy to handle these fraudulent attempts is always the same. Do not click a link unless it’s part of an active conversation. IF you find yourself on a Microsoft looking landing page, always look at the URL!
For a professional approach against such cyber threats, please reach out to StratusPointIT. Keeping your enterprise, your people, and your data safe is our commitment.