How Safe Is Your Law Firm From Data Breach?
With the pressure of minimizing data security breach threats mounting on firms, law firms are expected to set aside a considerable percentage of their budget to tackle information security challenges. According to a survey released by Chief Cost Management (CCM) with the sample comprising primarily of major companies, law firms are expected to spend nearly $7 million on enhancing in-house security by identifying security gaps in their networks.
Identifying cybersecurity priorities and knowing what makes a reasonable investment will help law firms gain the highest returns on their information security budgets. Otherwise, they risk spending too much and draining firm profits, or spending too little and jeopardizing the privacy and integrity of their information assets
–Len Levy, President, CCM
According to the report from CCM, more than two fifths of the companies surveyed have annual gross revenues between $100 million and $500 million. Law firms have considerable information assets, which, if lost due to a data breach, can significantly compromise their business integrity. Jerry Brandt, who wrote an article in 2012 regarding the bleak security conditions of law firms, referenced a study highlighting that more than 80% of law firms do not employ two-factor authentication and nearly 60% do not encrypt their laptops.
Managers, therefore, need to ask critical questions to ensure the safety of their law firm. Here are 5 questions every law firm should ask to assess their security risk level.
What level of confidential information do we collect?
For any business to determine its level of data security risks, it should first consider the type of information it stores on its data servers. If the stored data is highly sensitive and cannot be replaced or substituted easily, then the risk of a data breach can be regarded as very high. Law firms in particular are a trove of confidential information, which if stolen can mean immense financial and legal ramifications. Data pertaining to confidential information about clients, their weak points, clients’ intellectual property relating to patents and copyright information, client’s contact and address details, and confidential attorney-client information are stored on the networks of law firms.
Law firms and lawyers are required to meet a number of legal responsibilities to ensure that sensitive client information is not compromised in any manner. If a data breach occurs that leads to the loss of such essential information and data, a company could face a number of legal problems.
Which third parties gain access to our data?
Another factor to consider is the number of third parties that can acquire, access, and exploit a company’s confidential data records. Lawyers, for instance, are frequently required be on the move and work from their laptops. There is a possibility that third parties such as employees, friends, and clients themselves can gain access to important files and folders pertaining to a case and steal important information that can lead to a successful case.
The American Bar Association in 2011 urged lawyers to safeguard communications between them and their clients from unauthorized disclosure from the lawyer or other persons. Also, in 2010, the State Bar of California questioned whether the confidentiality between the client and the lawyer was compromised if the technology used to store the information was exposed to unauthorized access.
The issue was raised after an attorney used his laptop to conduct research from his home by using internet from a public Wi-Fi network and communicate to the client via e-mail. The California Bar considered the attorney to have acted incompetently and urged that he take appropriate steps to fortify sensitive information from others.
Who are the main stakeholders?
Businesses should also take into account the impact of a data breach upon its various stakeholders. In the case of law firms, the main stakeholders are the clients. However, there are also a number of other stakeholders that can be impacted such as board members, regulatory authorities, the press, and investors.
In the case of a data breach, it is important to outline in advance which stakeholders should the loss of data be communicated to first. Law firms would first report the news of a data breach to their clients, then to their board members and law enforcement agencies.
The law firm Foley & Lardner for example, provides 24/7 hotline 365 days a year to enable clients to speak with a designated data security attorney to provide counseling on what to do during the first stages of a data breach.
Have we experienced a data breach in the past?
Previous incidents of data breaches can also reveal a lot about the security condition of a firm. Revisiting the details can provide important learning tools such as indicating which measures worked well and which did not and the areas for improvement. Perhaps a firm did not have the assets to invest in a next generation firewall or implement an advanced company-wide network security program.
Furthermore, firms should delve into the minute details of how third parties gained access to the data, the channels used, whether the breach occurred internally or externally, and the location of the hacker.
How do we prevent future attacks?
Businesses need to embrace the fact that there is no fail safe button for data breaches and must ensure that any data breach that occurs is detected and managed quickly. The security team can investigate the root cause of previous incidents and implement or upgrade their intrusion detection systems and encryption methods to safeguard their data from sophisticated malicious software programs.
More importantly, it needs to ensure that employees are provided with an on-going training that incorporates the latest security measures and viruses that all need to be aware of. Attorneys need to make sure that they do not conduct any research on and for clients without using a highly secure internet connection and that e-mail are checked on a daily basis for any indication of malicious activities.
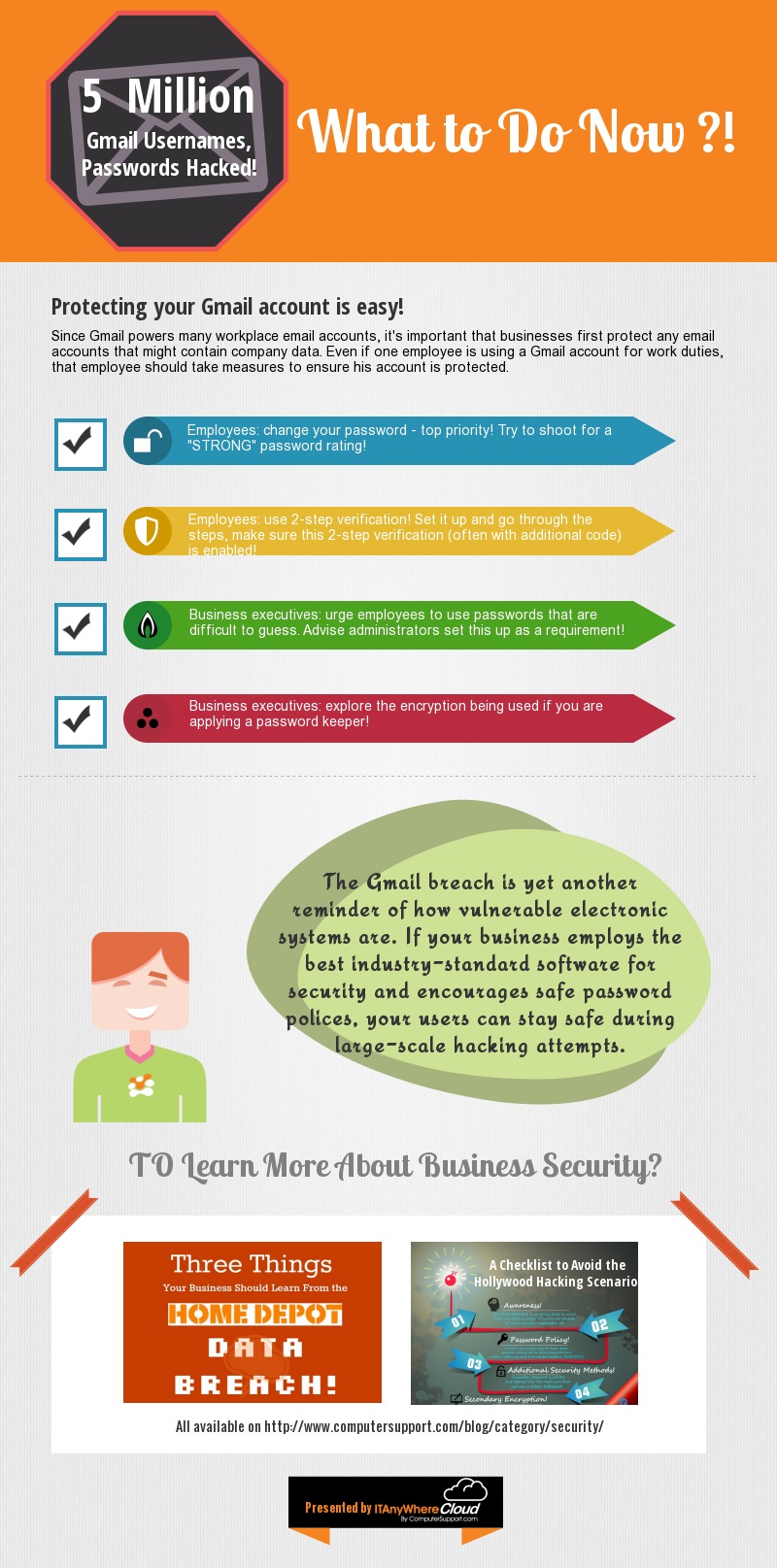
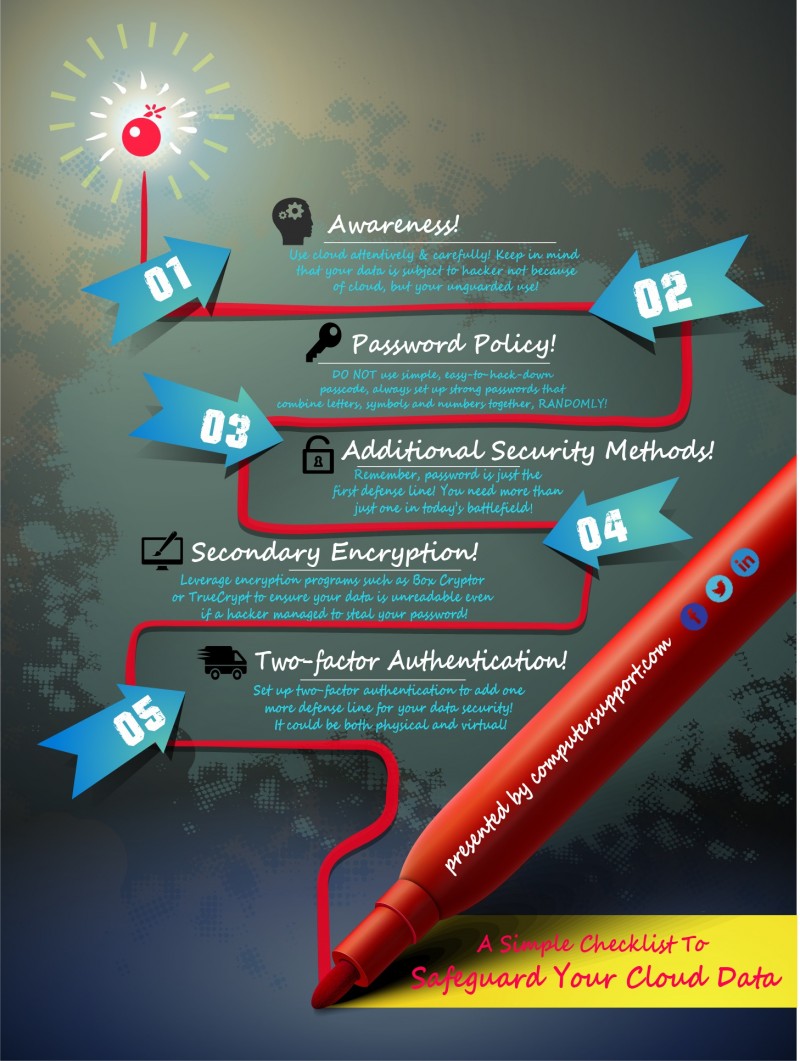
Other measures such as using two-factor authentication, passphrases, and having a periodic data backup and recovery routine should also not be overlooked.