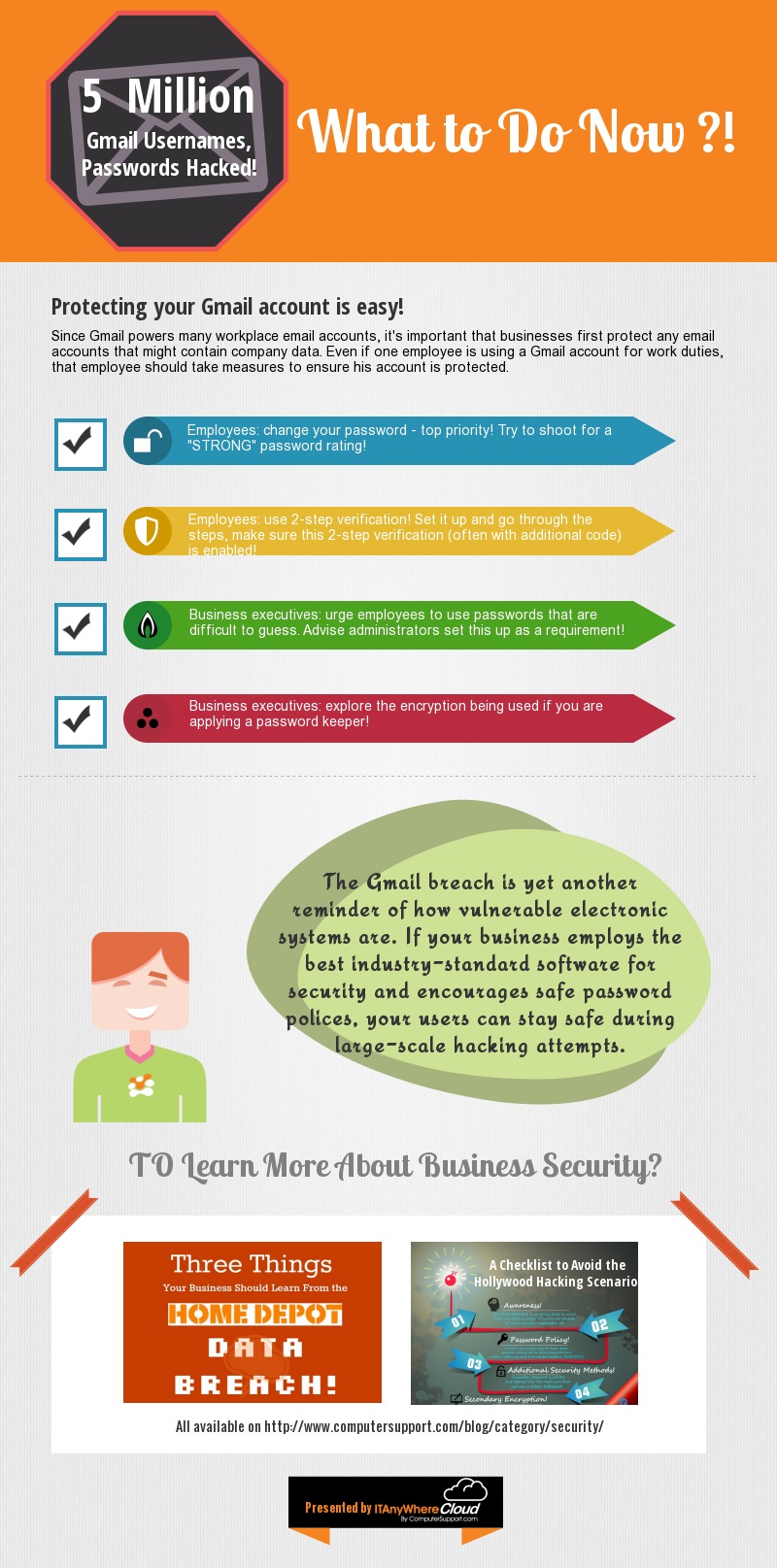
Dropbox Software Glitch: Lost Files May be Restored, What About Lost Confidence?
Mr. Murphy (of Murphy’s Law fame) has a way of seeing to it that data is lost when you need it most, and he is apparently undeterred by the Cloud Computing Revolution.
Still reeling from the iCloud breach, the Cloud Computing industry faces another PR hit – lost files due to a software glitch in the popular Dropbox application. The glitch is the latest in a series of incidents involving Dropbox, including an August 2012 security breach in which customer email addresses were stolen from Dropbox employee’s accounts, and recent concerns about Dropbox’s approach to addressing security vulnerabilities and notification of breaches.
Kudos to Dropbox for their response to this latest incident: a prompt mea culpa, a succinct explanation of the problem and who is affected, a quick software patch, and a free upgrade to the Dropbox Pro product. According to a company post on Hacker News, the file loss occurs if you use the Selective Sync features and the application is shut down or restarted when a selective sync is in progress. Dropbox has patched the desktop client, retired older versions of the Dropbox client, and ensured that users have the patched version. Affected users may receive a free one year subscription to the Dropbox Pro product which offers basic collaboration features and 1 TB of storage (normal pricing is $9.99 a month or $99 a year).
Some users report years of lost data. One case in particular has gone viral; that of Jan Čurn, co-founder and CTO at photography software platform VirtualRig Studio. Čurn has used Dropbox since 2009 and reports losing 8,343 files stored over that five year period. While the whereabouts of Čurn’s files have yet to be determined, Dropbox has been able to restore some user files, contacted affected users, and provided listings of restored files. It remains to be seen how much data can be restored.
It is important to note that the software bug is not related to security or malicious hacking, and that the bug affected personal users and not business users. Cloud storage products for Business Use require flexible user and file permissions setup, state of the art encryption standards, history logging, and remote administrative features. An example is the Secure.Share product from ComputerSupport.com. Aimed at small to medium sized business, it offers military grade, 448-Bit Blowfish encryption. Data is encrypted both in transit and at rest using SSL, and two factor authentication can be utilized. Accounts are managed from a single dashboard, and versioning and update notification features similar to Microsoft SharePoint are available for document collaboration. Additional security and administrative features include File History Sharing and remote data wiping.
Unfortunately for the affected Dropbox users, many used Dropbox as their sole document repository. The takeaway (painfully learned by the affected Dropbox users) is that personal cloud storage is not a substitute for regular backups. You’ve heard it before (and like me, have ignored it and paid the price) – regularly back up critical data and ensure it is two separate locations. This was true in the era of 5 ¼” inch Floppy Disks and is true today.