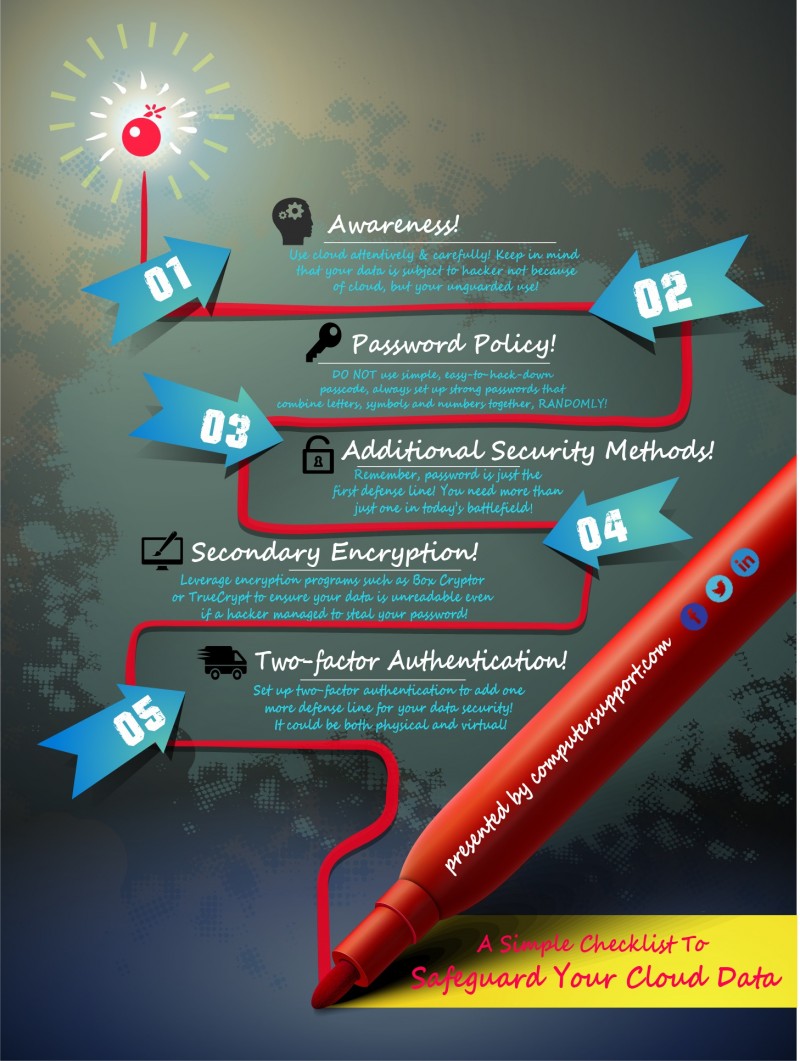
3 Things Your Business Should Learn from the Home Depot Data Breach

Experts say it may be the biggest data breach in U.S. history involving consumer credit and debit cards, with customer data stolen from more than 2,000 stores across the U.S. Home Depot is currently investigating the possible breach, which is believed to have possibly affected more than 40 million payment cards. Last year’s Target breach, which made national headlines and had a negative impact on the company’s stock, impacted more than 70,000 payment cards.
The reports are bringing concerns from consumers, who aren’t sure if their own cards may be affected. But businesses of all sizes should be concerned, as well, because the September 2nd warning of “unusual activity” to Home Depot from its bank could happen to any business. Before it happens to your organization, here are three things you can learn from the news about Home Depot’s data breach.
Data Security Should Be Tightened
While no amount of security is impenetrable, a business can protect itself by employing the latest security on each server that holds customer data. For retailers and ecommerce sites that use payment processing service providers, it’s important to contract with respected providers who employ the latest security to keep your customer data safe.
Data Breaches are Expensive
When the dust settles down on the Home Depot scandal, the company will still face months of backlash from the negative publicity. Target is still feeling the aftereffects of its December 2013 data breach, having lost the trust of the public and its investors. For months after the security issue, some customers are hesitant to use a credit card while shopping at an affected store, even after a business assures customers things are once again secure. The damage to a brand’s reputation can be financially devastating, potentially even forcing smaller businesses to close.
Microchips are Essential
Even as the news about these data breaches emerges, financial institutions are issuing cards with microchips that help prevent fraud. Merchants must upgrade to new terminals to accept these new cards, but once installed, these microchips will interact to identify the card, protecting credit card data and reducing the risk of data theft.
If your small business deals in customer payment information, it’s important to take as many measures as possible to protect that information from a data breach. Breaches can be extremely costly, potentially dooming a business to failure, so the future of a company may rest on its data protection procedures.