CMMC Compliance 2021
Who needs to comply?
By 2026, all contractors of the Department of Defense must comply with CMMC (Cybersecurity Maturity Model Certification) except commercial off-the-shelf software providers. This is mandatory for all subcontractors and every supplier the prime contractor works with across their entire supply chain.
Each contract will specify the CMMC level that each contractor must meet, so contractors on the same contract may have different CMMC requirements.
Differences Between CMMC & NIST 800-171
CMMC level 3 is based on NIST 800-171 compliance, which included the cybersecurity standards for Defense Industrial Base (DIB) contractors prior to CMMC.
Contractors must also meet all security controls in NIST SP 800-171 or provide a Plan of Actions and Milestones (POA&M) for compliance. A POA&M describes the specific measures that a DIB contractor will take to correct the deficiencies discovered during the security assessment.
NOTE! The shift from self-assessments to independent third-party assessments for cybersecurity compliance is one of the most important differences between NIST 800-171 and CMMC.
CMMC Third Party Assessment Organizations (C3PAOs) will now conduct these assessments.
CMMC adds 20 more new security requirements to Level 3 in addition to the 110 requirements already detailed in NIST 800-171. CMMC requires subjects to meet both sets of requirements for good cybersecurity practices.
CMMC and NIST SP 800-171 regulations will coexist until the Department of Defense completes the CMMC roll-out. The number of DoD contractors subject to CMMC will increase over the next few years, while the number of defense contractors requiring NIST SP 800-171 compliance will only decrease.
The CMMC Levels
The CMMC level that the Department of Defense requires of its contractors depends mostly on the sensitivity of the data these contractors will have access to.
CMMC Level 1
Level 1 requires companies to perform specified practices that focus on the protection of Federal Contract Information (FCI). So, level 1 only includes practices that meet the basic requirements as stipulated in 48 CFR 52.204-21.
CMMC Level 2
Level 2 practices are also known as intermediate cyber hygiene practices. They consist of a subcategory of the requirements specified by NIST SP 800-171. Level 2 practices focus on protecting controlled unclassified information (CUI).
NOTE! Controlled unclassified information is government owned information that requires protection consistent with applicable laws and regulations.
CMMC Level 3
Level 3 requires the organization to establish and maintain a plan to manage the activities needed to implement cybersecurity good practices. This plan can include information on a variety of specific topics, including goals, missions, projects, training, etc.
The cybersecurity practices at this level are considered good cyber hygiene practices and focus on the protection of CUI. Also, they include all security requirements that NIST SP 800-171 specifies, as well as other 20 security practices added specifically for CMMC level 3 to mitigate threats.
Defense Federal Acquisition Regulation Supplement (DFARS) clause 252.204 – 7012 adds few extra requirements, as for instance, how to report security incidents and strengthen the supply chain.
CMMC Level 4
Level 4 requires an organization to periodically review the effectiveness of its security practices. It also requires organizations to regularly inform upper management of the status of their information systems.
Level 4 practices are considered proactive and focus on the protection of CUI from advanced persistent threats (APTs). They also include a subset of other requirements from the draft of NIST SP 800-172 and other documents. These practices will only improve an organization’s ability to detect and respond to security threats.
CMMC Level 5
Level 5 certification implies that the contractor meets all level 1 – 4 requirements.
Level 5 requires 171 security controls and helps companies optimize their processes to ensure a standardized implementation across the entire organization. Practices at this level focus on CUI protection from advanced persistent threats. These advanced practices will increase the sophistication and depth of the organization’s cybersecurity capabilities.
CMMC 2.0
On November 4th, 2021, the Department of Defense announced “CMMC 2.0” to maintain the program’s goal of protecting sensitive data, while simplifying the CMMC standard and providing clarity on cybersecurity regulatory, policy, and contracting requirements. The standard will move forward with just 3 levels instead of 5 – foundational, advanced, and expert.
NOTE! CMMC 2.0 will allow all companies at Level 1 (Foundational) and a subset of companies at Level 2 (Advanced) to prove compliance through self-assessments similar to NIST 800-171 requirements. Level 3 (Expert) organizations will be assessed every three years by Defense Industrial Base Cybersecurity Assessment Center (DIBAC) assessors.
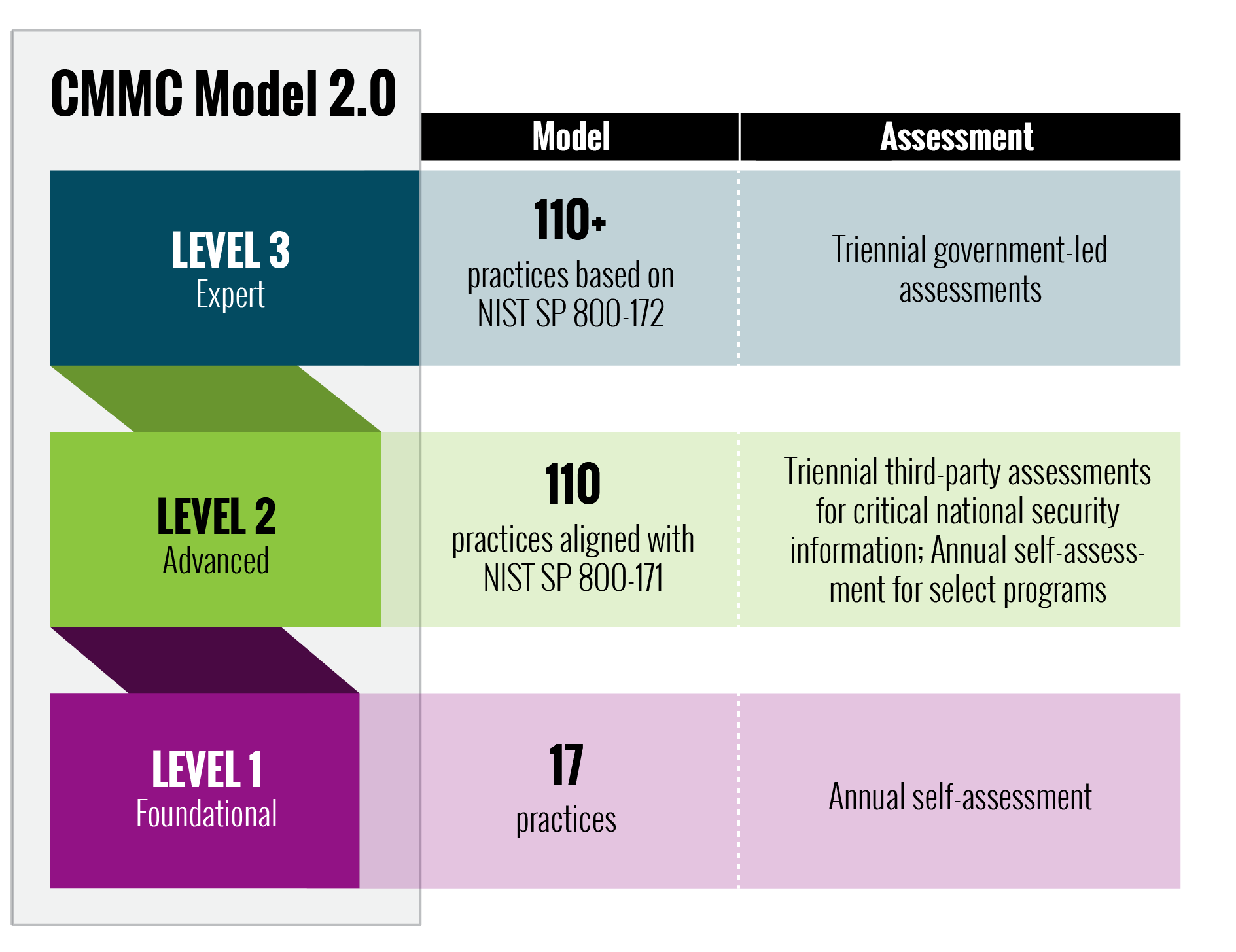
Under CMMC 2.0, the level 2 will be divided into Critical to National Security Information and Controlled Unclassified Information. Is not yet clear what companies can perform self-attestation and which ones require a C3PAO. The rulemaking process is still ongoing therefore, CMMC 2.0 will not be enforced right away. Organizations will be required to comply once the forthcoming rules go into effect.
StratusPointIT will provide your organization with guidance to achieve the necessary compliance level. Contact us today for more relevant information.


